Cut The Cloud Strings Attached to Plug-and-Play Surveillance Cameras
Many of us are excited about the modern AI powered security camera systems that give us peace of mind while away from home or workspace. It is far more effective and economical for automated security systems to recognize and alert on important events such as burglary or fire rather than dedicated human eyes watching endlessly uneventful monitors.
Plug-and-Play with Proprietary Vendor Cloud Service
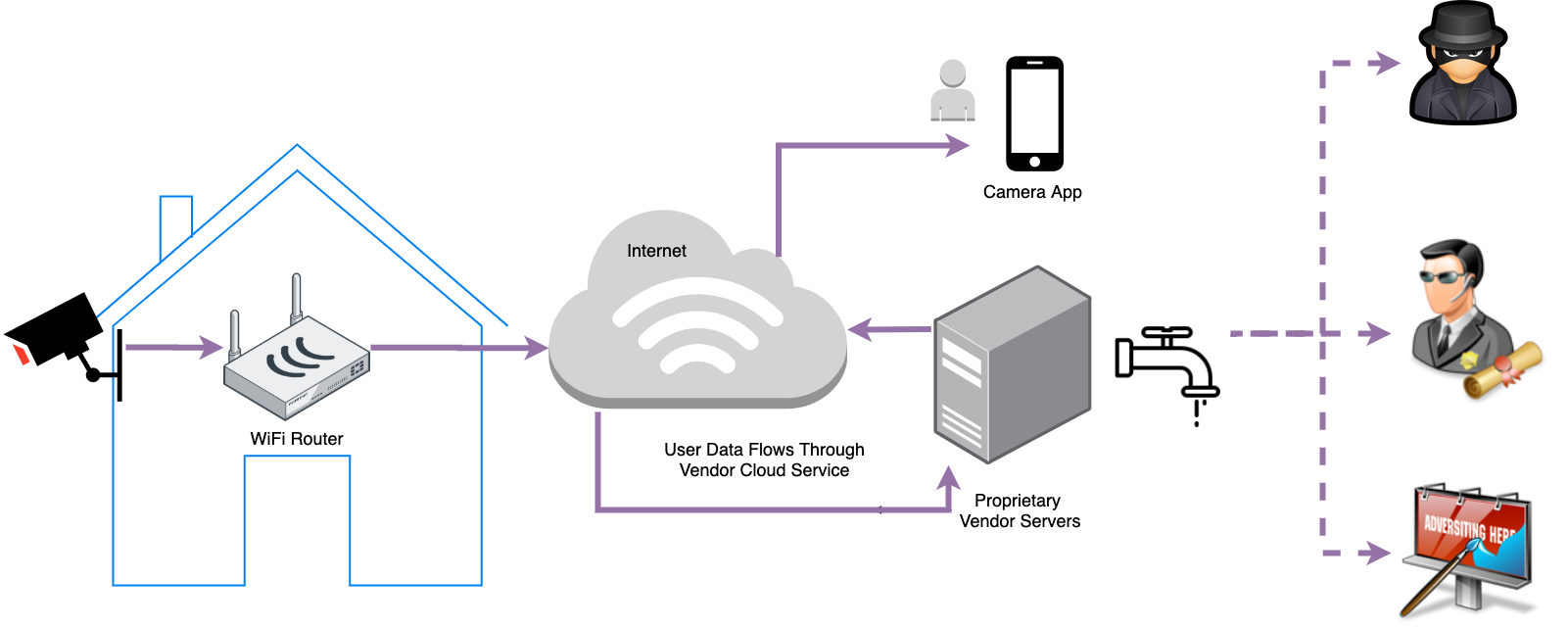
Most popular solutions that have emerged on the market in recent years offer easy plug-and-play experience attached to a proprietary cloud service. By design, these systems upload, store and process camera footage in their vendor cloud. The ease of use is a major benefit. However exposing user data to the public cloud comes with serious privacy issues. Despite regulatory pressure, sizeable fines in the billions of dollars and the subsequent efforts by vendors to protect user privacy, nearly all - big and small - fail to deliver. A few notable examples of data privacy violations:
- Leveraging user data for targeted advertisement.
- Sharing data with law enforcement without user consent.
- Sending data to foreign governments.
- Leaking user data due to product bugs.
- Data breach by hackers.
The following diagram illustrates a typical architecture of cloud attached security cameras. Here is a related discussion on Quora. Plug-and-Play convenience at the expense of trusting vendors with user data.
Direct Connectivity with Advanced Firewall Configuration
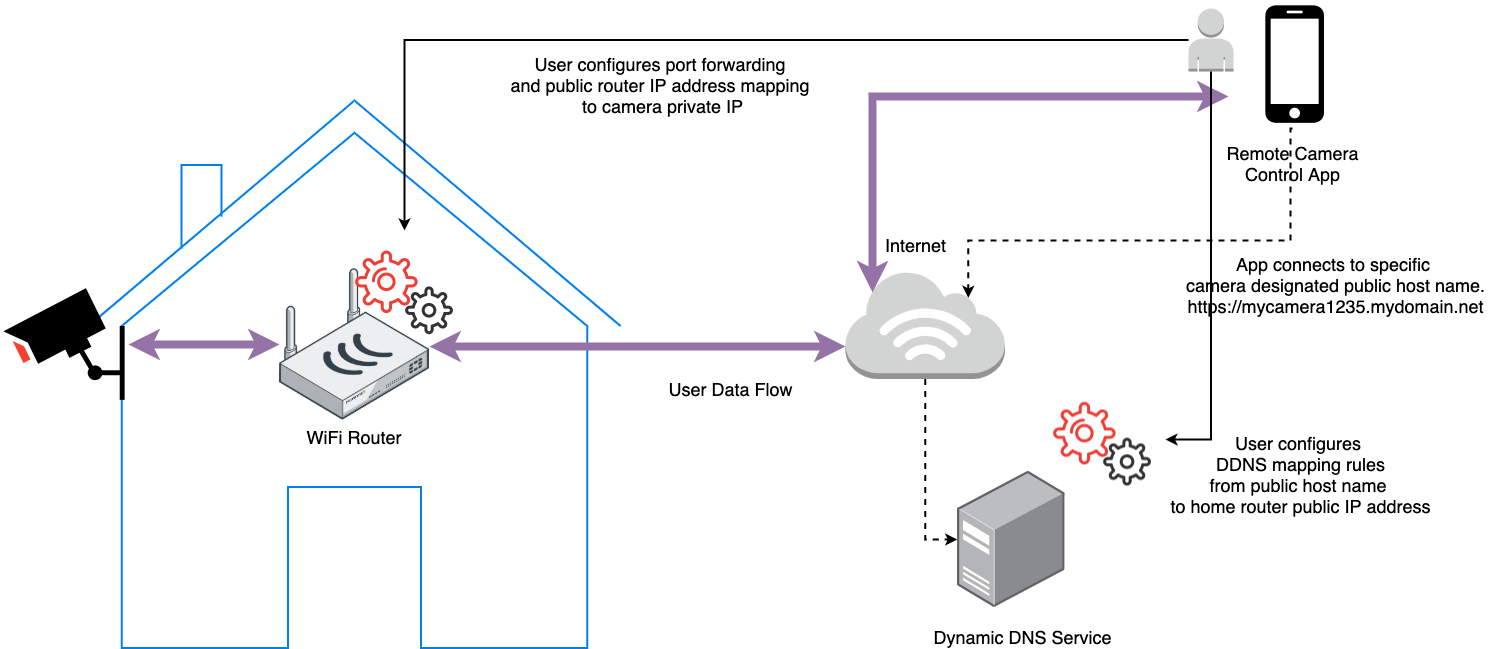
An alternative approach is to not use a proprietary vendor cloud to store, process and share camera footage. Instead enable users to directly connect to their security systems at home. Direct connectivity from user’s mobile device to their private IoT device residing behind a local firewall avoids the cloud security issues. However its a much bigger technical challenge than connecting to a public web service.
A typical technical solution requires advanced user knowledge of router configuration, port forwarding, DDNS, ISP policies and secure tunneling. Quite an effort compared to the plug-and-play convenience of cloud attached systems.
Plug-and-Play without the privacy compromising cloud service
What if there is a way to keep things plug-and-play easy, without compromising privacy?
Fortunately technology evolves fast and we have arrived at a time when this is possible. Below we will go over the solution used by Ambianic.ai - an open source ambient intelligence project.
Ambianic provides an Airdrop-like user experience connecting its Progressive Web App - Ambianic UI to a locally installed Ambianic Edge device.
Users can access Ambianic UI from anywhere and connect securely to their private Ambianic Edge device. They can also install it as a native desktop or mobile app on their favorite client device.
Ambianic Plug-and-Play Discovery
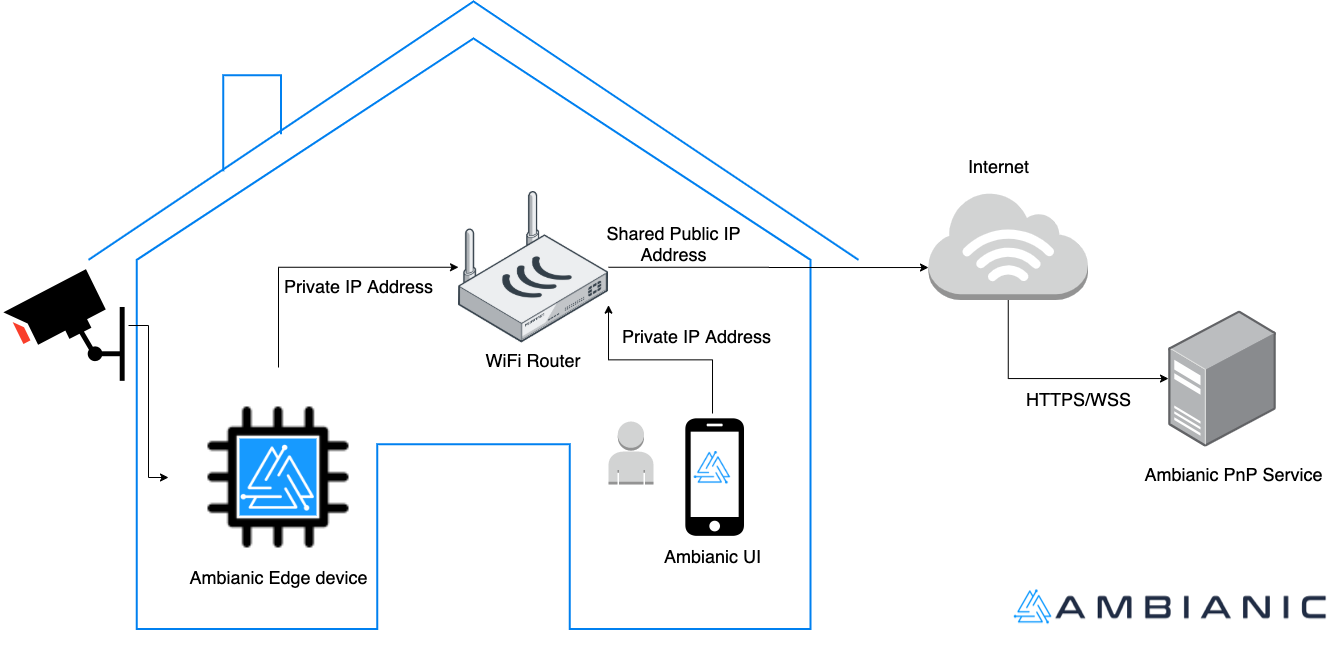
When the user starts Ambianic Edge for the first time on their local network, they are asked to access Ambianic UI from a client device that is also connected at the time on the same WiFi/LAN. Both the Edge device and UI register with the Ambianic PnP service, which performs an ephemeral registrar function. Its a simple matchmaking function which relies on the following assumptions:
- Users secure their local area network thoughtfully and only allow trusted devices to join.
- Users secure access to their client devices: mobile phones, laptops, desktops.
- Devices on the same local network share the same public IP when accessing public web services.
Through the Ambianic PnP registrar, UI and Edge are able to exchange each other’s unique identifiers (crypto strong UUID4 strings). The following diagram illustrates the PnP discovery architecture:
Ambianic Remote Connectivity
Why do Ambianic UI and Edge exchange their private identifiers? How will that help them connect when the user is on the road?
Its time to introduce WebRTC. WebRTC is a secure peer to peer (p2p) communication protocol and HTML5 browser API that allows browser apps to communicate directly with other browsers and IoT devices. WebRTC solves a number of very hard problems, such as:
- Bi-directional p2p Real Time Audio, Video and Data Channel Communication channels
- Complex network firewall traversal. Also known as Network address translation (NAT) traversal
- End-to-End Security
- Low packet latency
- Resilience to varying network bandwidth
- Native browser support. No custom plug-ins.
It took nearly 10 years of real world testing, iteration and adaptations to edge cases. As of December 2019 the W3C WebRTC 1.0 Recommendation is official! Even better, its implemented natively in all major modern browsers: Chrome, Safari, Firefox, Opera, Edge. Multiple independent Open Source implementations of WebRTC are actively being developed for C, Java, Go, and Python.
While 100% interoperability and edge case polishing of the implementations will take more time, our results shows that WebRTC is ready for the use case at hand. For the purpose of Ambianic UI and Ambianic Edge connectivity, we use the browser WebRTC stack and the Python aiortc implementations with an additional abstraction layer from PeerJS browser and PeerJS Python.
Here is a diagram of the Ambianic remote access architecture:
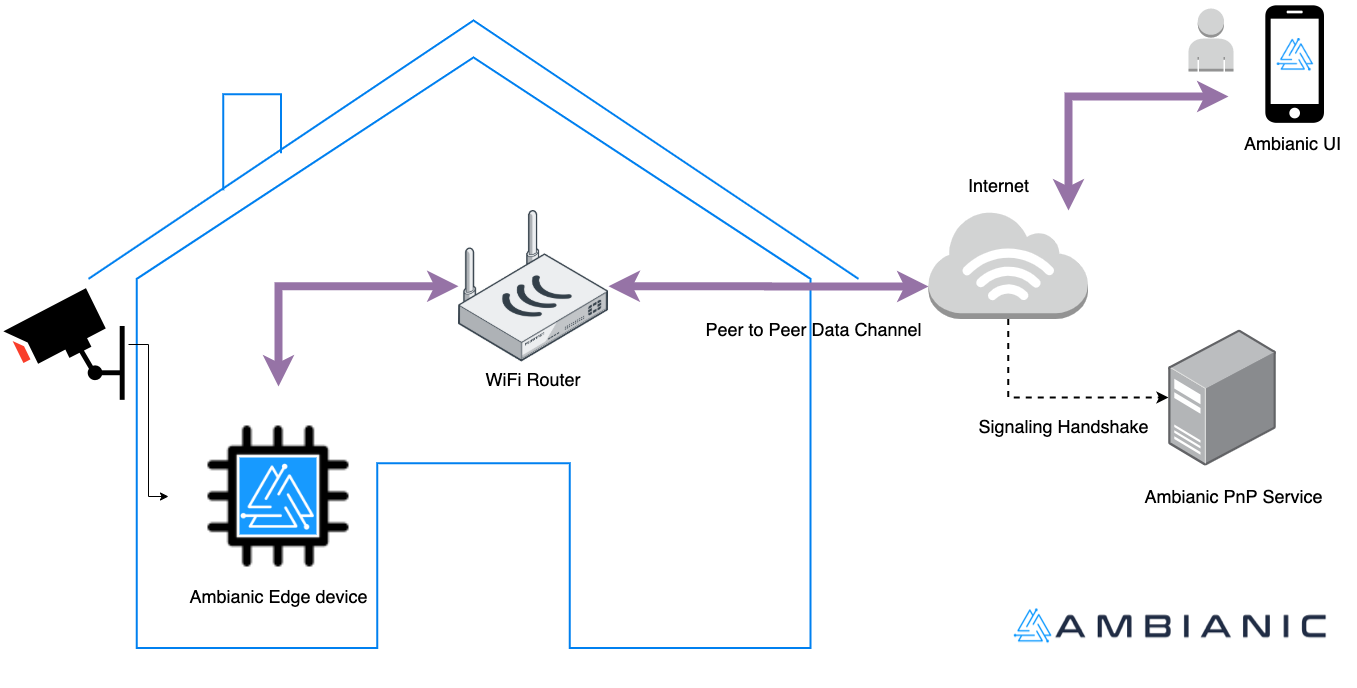
The diagram is simplified for clarity. It shows the essense of the remote connectivity service over WebRTC. Once the two peers in the communication channel Ambianic UI and Ambianic Edge discover each other’s UUID, they are able to open a signaling channel over HTTPS and Secure Web Sockets (WSS) via Ambianic PnP and negotiate the most direct possible routes to each other for their secure data exchange. At no time is user data exchanged outside a negotiated p2p channel.
This approach has a few bonus benfits over typical vendor cloud attached services in addition to reducing privacy risks:
- Lower latency. Important alerts travel in real time directly from the edge device to the UI using the shortest possible Internet route. No detours and short stops at third party cloud services.
- Lower architecture complexity. There is no need to build and manage a complex cloud service which is in the critical communication path.
- Higher availability. The Ambianic PnP service has no persisted state. Its easy to maintain, easy to scale and easy to replace any failed nodes.
- There are no extra costs associated with user traffic passing through the cloud service.
- There are no costs for cloud storage, data processing and other middleware functions.
- To re-iterate one more time, there is no public cloud service exposed to data breach attacks.
If you’d like to get a feel how this all works, feel free to follow the 5 Minute Quick Start guide.
You are also welcome to dive in the code and learn more about the mechanics of the Ambianic architecture. All of the code is 100% Open Source under the permissive Apache 2.0 License.
What’s the catch?
This approach is only as strong as its weakest link. If the basic assumptions don’t hold then the user data is not safe:
- WiFi networks have been around more than 20 years. Yet they are still prone to security breaches exploiting poor security hygiene.
- Personal device security is another common vector of attack. If its compromised then access to the Ambianic Edge device is also exposed.
We will keep eyes peeled for community ideas and contributions to further protect user privacy. Some suggestions on the table include two factor authentication (2FA) for access to Ambianic Edge and biometric login for Ambianic UI (fingreprint or face recognition).
If you have opinions on the right balance of usability vs safety, let us know on our twitter channel. Comments, bug reports and contributions are most welcome!
PS: For a more technical coverage of the Ambianic.ai’s unique privacy preserving architecture, take a look at this artcile published by WebRTCHacks: Private Home Surveillance with the WebRTC DataChannel.
PPS: Many thanks to @robmarkcole and @JohnJSenay for their feedback on the early draft of this post.*